Internet of Things (IoT) is one of the most evolving fields in the last two decades. IoT extends the purview of networking from anyplace, anytime to anything by connecting devices such as sensors, actuators, smart objects, etc. It is expected that more than 1.25 billion devices will be connected to the internet by the year 2030. These devices operate on wide range of communication technologies including Radio Frequency Identification (RFID), bluetooth, ZigBee, Wi-Fi, wireless LAN, Low-Power Wide-Area Network (LPWAN), Fiber To The x (FTTx) and cellular (3G/4G/5G) introducing heterogeneity in IoT networks. There are many research challenges that exist in the field of IoT today that prohibit the realization of many innovative solutions. Some major issues relate to interoperability, scalability, security, and inadequacy of efficient techniques to process huge online data in nearly real-time.
Machine Learning in IoT
IoT devices are expected to generate huge amounts of data [2]. However, IoT devices are constrained, because of limited battery life, CPU power and memory, thus, incapable of executing Machine Learning (ML) algorithms to process enormous data locally. Many solutions have been proposed in the literature suggesting connecting IoT devices to cloud data center via IoT gatewa. The data from various devices is then stored and processed centrally in the cloud data center. Though feasible and useful, this architecture poses some problems. Many applications such as emergency response systems and driverless cars, require faster data processing and near real-time response. Carrying all the data to the cloud data center introduces latency. Another issue relates to inefficient consumption of network bandwidth as all data may not be useful for processing. To overcome these challenges, a distributed architecture in the form of edge computing has been proposed which a powerful server, called ‘edge server’, resides close to IoT devices producing data. These edge servers process data efficiently near to the data sources, thereby providing faster responses and saving network bandwidth. Edge servers can contact cloud data center in case more resources are required.
IoT devices like sensors generate data continuously over time. Such data is called data stream. Moreover, the data points are correlated to each other. A new clustering method called DenStreamED, that uses the embedding dimension to represent the incoming data into an embedded space in which stream based clustering is performed. Such algorithm can be implemented in edge server. Another popular ML paradigm in context of IoT is Federated Learning (FL) where a collaborative model is learnt without sharing data. A Horizontal Federated Decision Tree Learning (HFDTL) system is proposed in one of the works which can build a collaborative model from evolving data streams in federated environment such as that of edge network where IoT gateways play the role of edge nodes processing data locally and edge server aggregates the local models using newly proposed majority-based aggregation algorithm. In another work, a federated clustering method, called FedCLUS, that allows to learn clusters from distributed homogeneous data without sharing it. The distinguishing characteristic of the Fed-CLUS method is its ability to retain, merge and discard original clusters sent by data owners. FL is one of the most active areas in IoT research now a days.
IoT Traffic Analysis and Modeling
Traffic in IoT network is qualitatively different from that of traditional voice and data networks as devices produce traffic in place of human users. Many statistical studies on IoT network traffic establish the presence of gamma, beta, lognormal and other probability distributions describing inter-arrival time of packets in contrast to widely observed exponential distribution (or Poisson arrival process). The existence of multiple heterogeneous arrival patterns in IoT network is because of the diverse devices originating traffic. This necessitates to develop new analytical traffic models for IoT networks. Traffic models help in
Many new analytical traffic models like Gamma/M/1, Gamma/M/1/N, LN/M/1, GE/M/1 etc. have been proposed in the IoT literature. Besides, simulation studies to analyze the impact of heterogeneous traffic on quality-of-service parameters like loss probability, delay etc. are also available. In spite of this, IoT traffic engineering is still in infancy and more robust and complex models need to be developed.
Security in IoT Network
With the popularity of IoT in various domains including mission critical and personalized areas, security in IoT networks has become a major topic of interest. There are many reasons why IoT network are more prone to attack than the traditional computer network:
All the above reasons pose a lot of challenges in ensuring security in IoT networks and they become vulnerable to intrusions.
Discovery Services in IoT
In order to realize and exploit the complete capability of IoT by allowing inter-operability among heterogenous devices, one of the aspects relates to identification of the desired device or devices, commonly known as device discovery in the network. Searching for a device in a heterogeneous IoT environment requires one to either know the physical identity of the device or domain name of the organization owning the device. Other than this, there are instances when devices are to be searched based on criterion like location, functionality, owners i.e. the attributes characterizing devices. The existing discovery architectures can be divided into two broad categories: centralized and distributed. Centralized discovery architectures suffer from known drawbacks such as non-scalability and single point of failure. The Constrained Application Protocol (CoaP) allows devices to search centralized resource directory (RD) for services and resources. In contrast, devices search for other devices without going to a centralized repository in distributed architecture. One common problem of distributed discovery architectures is that they result in huge amount of network traffic. To address this, an attribute based distributed device discovery architecture has been proposed in the literature (given below) where DSN (Discovery Service Node) is a directory of IoT devices in an access network.
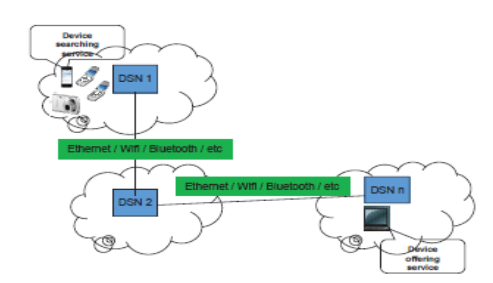
Device discovery is also needed in Semantic Internet of Things. An important issue in device discovery architectures is to ensure the scalability of the solution since IoT consists of billions of devices. It has been proposed in the literature to use clustering methods in directory of IoT devices to enable quick search. To this end, incremental and hierarchical device clustering method, HiCHO, has been proposed for managing IoT devices.
IoT-oriented Software Engineering
Rapid growth of IoT in various areas is not possible without software. IoT software are inherently different from traditional software because of the requirement of supporting multiple types of devices, heterogeneity, distributed and dynamic environment, always-on nature of the system. This has led to altogether new software engineering approach, called IoT-oriented software engineering. Researchers are trying to find a new paradigm of IoT software development. Besides, there are works like analyzing the defect distribution in IoT software which confirms the emergence of power-law behavior in defect distribution of IoT software akin to traditional ones. IoT-oriented software engineering is a relatively new research area and thus offers opportunities to new researchers.
Identity Management of IoT Devices
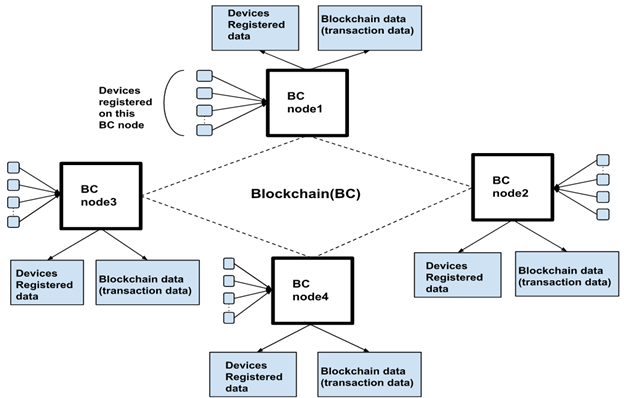
The number and complexity of interconnected devices in IoT is expected to grow considerably, leading tracking, monitoring and identification of each interconnected device to become a more challenging task. Therefore, efficient identity management techniques for IoT are the need of time, more in the context of Social Internet of Things and Web of Things paradigms. Many solutions have been proposed for identity management of single device as well as managing multiple identities of devices using blockchain. An illustration is given below: